Welcome to our ongoing blog series on iOS App Penetration Testing and Security, where we explore real-world case studies to better understand the challenges and vulnerabilities in today's iOS applications. In the previous blog, we delved into the risks posed by URL Schemes and the security concerns arising from using UIWebView in iOS apps.
In this edition, we'll examine two other critical aspects of iOS application security: the dangerous practice of hardcoding credentials and the potential exploitation of third-party libraries. Through our exploration, we'll gain insight into the mistakes developers often make when handling sensitive data while building applications and learn how to safeguard against malicious activity stemming from vulnerable external components.
Case Study 3 - Hardcoded Secrets in Ride-Sharing App
Summary:
A ride-sharing company developed an iOS app to connect drivers and passengers. The app used a third-party payment provider's API to facilitate in-app payments. However, the development team made a crucial mistake by hardcoding the API key and other sensitive information into the app's code.
Steps Followed:
- I downloaded the iOS app and decrypted it using reverse engineering tools. After unzipping the iOS application, I examined the source code using Hopper disassembler and discovered the hardcoded API key of the payment provider and other sensitive information.
- With the API key in hand, I gained unauthorized access to the third-party payment provider's system.
- I could perform actions such as providing fake payments for rides, refunding completed transactions, and accessing users' transaction history.
- I created a proof of concept demonstrating the vulnerability and reported my findings to the ride-sharing company.
Proof of Concept:
- By following the decryption steps mentioned earlier, you can reverse engineer the IPA file. Once this is done, utilize the Hopper disassembler to identify any hardcoded strings within the application, as demonstrated below:
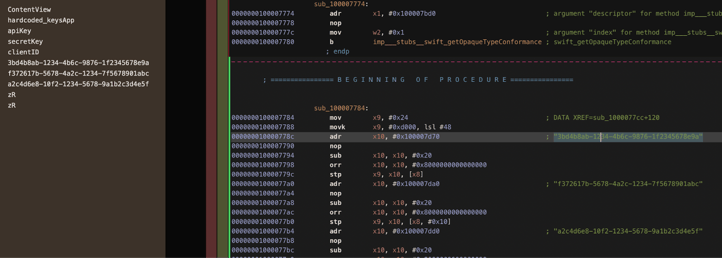
- You can observe all the hard-coded strings and secrets in plain text within the Hopper disassembler.
Important Lessons:
- Avoid hardcoding sensitive information, such as API keys, passwords, etc., directly into the app's code.
- Use secure storage and management practices for sensitive data, such as encryption and dedicated secret management services like Hashicorp Vault.
- Limit the scope and permissions of API keys/tokens to minimize the potential impact & blast radius of the data breach.
Case Study 4 - E-Commerce iOS App Exploitation Through Third-Party Exploitation
Problem:
An e-commerce company developed an iOS app for shopping for electronic appliances. While the application was designed in-house, the backend infrastructure was managed by a third-party cloud database provider. The cloud provider issued a certificate with a private key for an SSH connection to authenticate and securely access the backend resources. However, the development team made a critical mistake by embedding the certificate directly into the app.
Steps Followed:
- I downloaded the iOS app and extracted the .ipa file. Next, I unzipped the iOS application containing all the .plist, .json, .xml files, images, icons, and the third-party cloud database provider's certificate.
- Upon further investigation, I discovered the private key for accessing the backend infrastructure in one of the configuration files.
- I attempted to establish an SSH connection with the cloud provider's server. As a result, I gained access to sensitive data, including customer names, addresses, shopping lists, and preferred payment methods.
- I created a proof of concept and reported my findings.
Practical Steps
Note: You can perform this exercise on a standard iPhone. It does not require a rooted or a jailbroken iPhone.
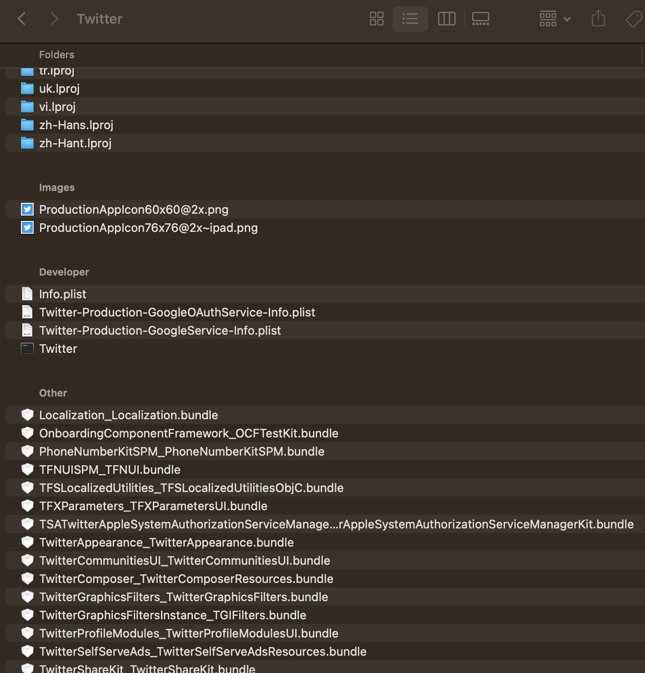
- Here is an example of what the Twitter iOS app may look like after being unzipped.
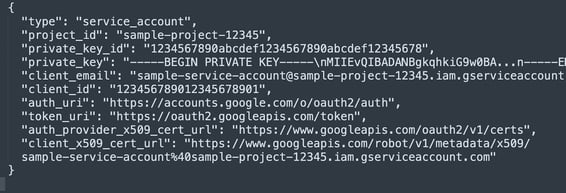
- The following sample configuration file contains sensitive information, such as an SSH private key and client email ID:
Impact:
- Fortunately, the e-commerce company's security team realized the severity of the issue and immediately took measures to rectify the vulnerability.
Important Lessons:
- Avoid embedding sensitive information, such as private keys, directly in the application source code; instead, use KMS solutions such as Vault & AWS KMS.
- Store sensitive configuration files and credentials securely, preferably on a server rather than within the app itself.
- Implement proper encryption for sensitive data, both in transit and at rest.
References
- Apple Developer Documentation - App Transport Security (ATS)
- Apple Developer Documentation - Secure Coding Guide
- OWASP Mobile Application Security Verification Standard (MASVS)
- OWASP Mobile Security Project - Top Ten Mobile Risks