Cyber attacks have not only increased in prevalence, but also in sophistication. This leaves businesses vulnerable and requires defensive planning to prevent attackers. Cobalt’s Red Teaming Services are here and by your side — along with a team of experienced consultants readily available to help outline a comprehensive plan of attack to meet your business’s security goals.
Adversary Simulation Process
In the adversary simulation process, a series of emulated attacks are carried out to provide a holistic view of specific vulnerabilities that should be on a company’s radar. Adversary simulation is a white box activity to ensure security teams are fully prepared to mitigate real potential attacks. This zero-stakes approach allows more advanced attacks in order to achieve certain goals, similar to a technical audit.
Red teaming engagements come from a zero-knowledge perspective, meaning the organization is typically not notified ahead of time of an attack, and the techniques, tactics, and procedures from real-world attackers are replicated. (Read more about red team versus pentesting with an indepth guide.)
“Threat actors can be persistent, motivated, and agile, and they use a variety of tactics, techniques, and procedures (TTPs) to compromise systems, disrupt services, commit financial fraud, and expose or steal intellectual property and other sensitive information.” (Guide to Cyber Threat Information Sharing)
Red Teaming Security Services
Red Teaming is an offensive security technique that evades current protection capabilities. More and more companies are conducting red team exercises as the emphasis on protecting organizational assets from cyberattackers grows.
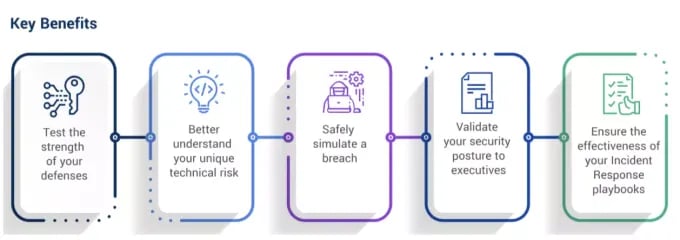
Understanding current weaknesses in security posture is just the beginning. Whether you’re looking to test the strength of your assets or simulate an attack to prepare for the future, Cobalt’s Red Teaming Services are ready to help.
Here’s what you can expect from a Red Team engagement:
Before: A well-defined scope and timeline are agreed on from the start, within the determined rules of engagement.
During: Through the Cobalt Platform and Slack channel, Cobalt provides consistent updates and open communication.
After: Test results and reporting are delivered and able to be discussed in detail as needed.
Red teaming is an extension of pentesting used to identify security weaknesses and give a clear look at what a motivated attacker can do when exploiting vulnerabilities. This way, businesses can understand their most critical risks and actively test defenses.
Being an extension of Cobalt’s modernized pentesting platform, our seasoned security experts value collaboration and transparency through each red teaming engagement. Chris Wallace, Security Liaison Engineer at Vonage, says one main benefit of the variety of skill sets available through Cobalt is the “community of pentesters that you can readily draw from. We don't have to hire more red team people, we can bring them on as needed.”
Learn more about how Cobalt’s Cybersecurity Services serve as the additional layer of defense your business needs to help strengthen your security posture. Learn more about the benefits of Cobalt’s Red Teaming Services, and read all about our other cybersecurity services here.

















%20(22).png)

